Blog Archives
Windows Server 2008 R2 – Active Directory – All Possible Deployment Types – DcpromoUI Answer Files – Reference
WaheGuru G Ka Khalsa, WaheGuru G Ki Fateh
In this Post, we list the answer files (and some of the main critical parameters in the answer files) created by DcpromoUI to be used as a reference.
DcpromoUI answer file – sourced from a New Forest Root Domain Controller promotion wizard:
; DCPROMO unattend file (automatically generated by dcpromo) ; Usage: ; dcpromo.exe /unattend:C:\Users\Administrator\Desktop\DcpromoUI win2008 r2.txt ; [DCInstall] ; New forest promotion ReplicaOrNewDomain=Domain NewDomain=Forest NewDomainDNSName=hello.com ForestLevel=4 DomainNetbiosName=HELLO DomainLevel=4 InstallDNS=Yes ConfirmGc=Yes CreateDNSDelegation=No DatabasePath="C:\Windows\NTDS" LogPath="C:\Windows\NTDS" SYSVOLPath="C:\Windows\SYSVOL" ; Set SafeModeAdminPassword to the correct value prior to using the unattend file SafeModeAdminPassword= ; Run-time flags (optional) ; RebootOnCompletion=Yes
DcpromoUI answer file – sourced from a New ADDITIONAL Domain Controller promotion wizard:
; DCPROMO unattend file (automatically generated by dcpromo) ; Usage: ; dcpromo.exe /unattend:C:\Users\Administrator\Desktop\DcpromoUI ADC.txt ; ; You may need to fill in password fields prior to using the unattend file. ; If you leave the values for "Password" and/or "DNSDelegationPassword" ; as "*", then you will be asked for credentials at runtime. ; [DCInstall] ; Replica DC promotion ReplicaOrNewDomain=Replica ReplicaDomainDNSName=globomantics.com SiteName=NewYorkHQ InstallDNS=Yes ConfirmGc=Yes CreateDNSDelegation=No UserDomain=globomantics.com UserName=globomantics.com\administrator Password=* DatabasePath="C:\Windows\NTDS" LogPath="C:\Windows\NTDS" SYSVOLPath="C:\Windows\SYSVOL" ; Set SafeModeAdminPassword to the correct value prior to using the unattend file SafeModeAdminPassword= ; Run-time flags (optional) ; CriticalReplicationOnly=Yes ; RebootOnCompletion=Yes
DcpromoUI answer file – sourced from a NEW RODC promotion wizard:
; DCPROMO unattend file (automatically generated by dcpromo) ; Usage: ; dcpromo.exe /unattend:C:\Users\Administrator\Desktop\DcpromoUI rodc.txt ; ; You may need to fill in password fields prior to using the unattend file. ; If you leave the values for "Password" and/or "DNSDelegationPassword" ; as "*", then you will be asked for credentials at runtime. ; [DCInstall] ; Read-Only Replica DC promotion ReplicaOrNewDomain=ReadOnlyReplica ReplicaDomainDNSName=globomantics.com ; RODC Password Replication Policy PasswordReplicationDenied="BUILTIN\Administrators" PasswordReplicationDenied="BUILTIN\Server Operators" PasswordReplicationDenied="BUILTIN\Backup Operators" PasswordReplicationDenied="BUILTIN\Account Operators" PasswordReplicationDenied="GLOBOMANTICS\Denied RODC Password Replication Group" PasswordReplicationAllowed="GLOBOMANTICS\Allowed RODC Password Replication Group" SiteName=NewYorkHQ InstallDNS=Yes ConfirmGc=No CreateDNSDelegation=No UserDomain=globomantics.com UserName=globomantics.com\administrator Password=* DatabasePath="C:\Windows\NTDS" LogPath="C:\Windows\NTDS" SYSVOLPath="C:\Windows\SYSVOL" ; Set SafeModeAdminPassword to the correct value prior to using the unattend file SafeModeAdminPassword= ; Run-time flags (optional) ; CriticalReplicationOnly=Yes ; RebootOnCompletion=Yes
DcpromoUI answer file – sourced from a NEW DOMAIN TREE promotion wizard:
; DCPROMO unattend file (automatically generated by dcpromo) ; Usage: ; dcpromo.exe /unattend:C:\Users\Administrator\Desktop\DcpromoUI.txt ; ; You may need to fill in password fields prior to using the unattend file. ; If you leave the values for "Password" and/or "DNSDelegationPassword" ; as "*", then you will be asked for credentials at runtime. ; [DCInstall] ; New tree promotion ReplicaOrNewDomain=Domain NewDomain=Tree NewDomainDNSName=test.com DomainNetbiosName=TEST DomainLevel=4 SiteName=NewYorkHQ InstallDNS=Yes ConfirmGc=No CreateDNSDelegation=No UserDomain=globomantics.com UserName=globomantics.com\administrator Password=* DatabasePath="C:\Windows\NTDS" LogPath="C:\Windows\NTDS" SYSVOLPath="C:\Windows\SYSVOL" ; Set SafeModeAdminPassword to the correct value prior to using the unattend file SafeModeAdminPassword= ; Run-time flags (optional) ; RebootOnCompletion=Yes
DcpromoUI –NEW Forest Root Domain deployment – Critical Parameters
ForestLevel=0 | Windows 2000 DomainLevel=0 | Windows 2000 ForestLevel=2 | Windows 2003 DomainLevel=2 | Windows 2003 ForestLevel=3 | Windows 2008 DomainLevel=3 | Windows 2008 ForestLevel=4 | Windows 2008R2 DomainLevel=4 | Windows 2008R2
DcpromoUI – various Domain Controllers types deployment – Critical Parameters
; New forest promotion ReplicaOrNewDomain=Domain NewDomain=Forest NewDomainDNSName=hello.com ; Replica DC promotion ReplicaOrNewDomain=Replica ReplicaDomainDNSName=globomantics.com SiteName=NewYorkHQ . ; Read-Only Replica DC promotion ReplicaOrNewDomain=ReadOnlyReplica ReplicaDomainDNSName=globomantics.com SiteName=NewYorkHQ ; New child domain promotion ReplicaOrNewDomain=Domain NewDomain=Child ParentDomainDNSName=globomantics.com ChildName=child01 ; New tree promotion ReplicaOrNewDomain=Domain NewDomain=Tree NewDomainDNSName=tree01.com
Hope this helps and Cheers ![]() | Your feedback is highly appreciated.
| Your feedback is highly appreciated.
WaheGuru G Ka Khalsa, WaheGuru G Ki Fateh
Copyright © 2013
For copyright purposes, VirtualizationMaximus.com is not in the public domain. The fact that this blog owner publishes an RSS feed does not grant any rights for republication or re-use of the material except in the manner described below.
All content in this blog created by the blog owner and his guest authors is the property of the blog owner and his guest authors and protected by international copyright laws and cannot be stored on any retrieval system, reproduced, reposted, displayed, modified or transmitted in any form, electronic or otherwise without written permission of the copyright owner except as noted below.
A brief excerpt of content that does not exceed 128 words or 512 characters may be quoted as long as a link is provided back to the source page on this blog and authorship is properly attributed.
Airtel Broadband – Beetel CPE Device – 450TC1 – MGMNT SSID – Hack – Exploit
WaheGuru G Ka Khalsa, WaheGuru G Ki Fateh
In this Post, we illustrate a possible hack – exploit with Beetel ADSL Routers/Modems (Broadband CPE) distributed by Airtel Broadband, INDIA – which once exploited, we can gain Subject’s (target) LAN network access and thereby WAN ( WAN- if operating in PPPOE/Router/NAT Mode & no custom IPTables rules and/or Network ACLs are defined).
CPE Device Model: Beetel 450 TC1
CPE Device Default Admin Credentials: admin | password
Tested Device Information:
RAS version: TM4-0Q-020__TME-0Q-020
System ID: $2.11.65.2(RE5.C21)3.12.7.0 20100628_V022[Jun 28 2010 14:44:06]
romRasSize: 1351290
system up time: 9:32:48 (347163 ticks)
bootbase version: VTC_SPI1.12 | 2010/09/09
Default Broadcasted SSIDs:
SSID1 – AIRTEL – SSID Index 1 – (when connected to this SSID – we can connect to Internet) (We can only Configure this SSID i.e. SSID with Index -1).
SSID2 – MGMNT – SSID Index 2 – (when connected to this SSID – we can only view CPE Device STATUS page and can’t connect to Internet (probably due to IPtables) (We can’t Configure this SSID or disable this SSID i.e. SSID with index – 2).
Exploit Summary: Connect to Secondary SSID (SSID with Index – 2) – MGMNT – (Airtel CPE Service SSID) in order to reveal Credentials associated with Primary SSID (SSID with Index – 1).
Procedure:
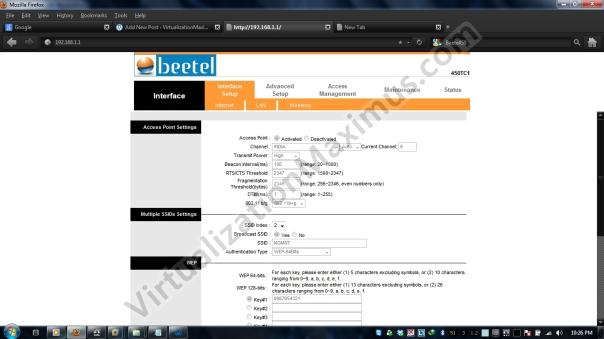
By default (with factory defaults), this specific Router broadcasts two SSIDs – one named Airtel and other MGMNT. Consumer can only modify Airtel SSID (with SSID Index 1) as per their requirements BUT can’t turn off MGMNT SSID (using SSID 1 or SSID2 or Ethernet) – as shown below.
MGMNT SSID by default broadcasts with WEP Encrypted Cipher HEX-10Digits (64Bits) with OPEN Authentication (WEP64 Security – OPEN) with WEP key set to “0987654321”, as show below:
Also note in Web Based Administration Page, all buttons are grayed out/disabled – so we can’t Configure/turn off SSID 2 (MGMNT).
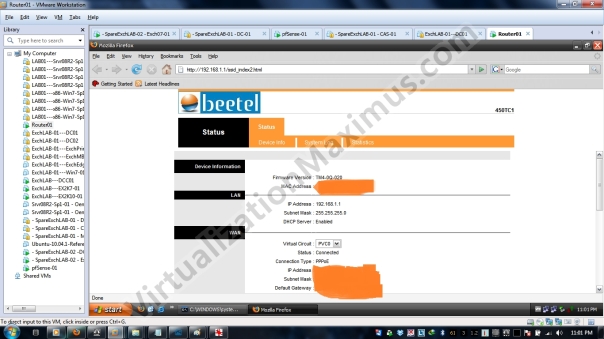
Now when we are connected to MGMNT SSID (using default WEP key – 0987654321), we will get an IP Addr from dhcpd DHCP Pool and we open Device Administration Page, CPE device detects that we are connecting using MGMNT SSID (Airtel CPE Service SSID), it will automatically redirect URL to http://x.x.x.x/ssid_index2.html (from http://x.x.x.x) – where x.x.x.x is IPv4 address of the CPE Device – which in our case (and default) is 192.168.1.1 – as shown below:
We login to MGMNT SSID using Default Credentials i.e. admin | password, and we presented STATUS Page of the device – also note that we can’t really Configure CPE Device when connected using MGMNT (because we are not entertained with full featured Device Administration version with MGMNT – but rather represented with only STATUS page – arbitrarily – we are represented with lite version).
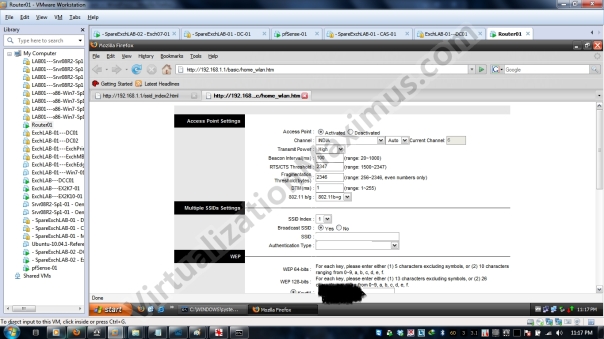
And here goes our exploit, we enter URL as http://x.x.x.x/basic/home_wlan.htm – and voila — we are represented with Page to configure Primary SSID — i.e. SSID which can route packets to WAN/Internet.
This exploit can be prevented by simply changing the default admin credentials (because we are using default admin credentials to log into Administration Page when connected to MGMNT [SSID Index – 2]) .
Our sole intent is to get Beetel 450TC1 Consumers (with specific firmware’s) Aware, Safe and Secure.
Airtel ISP can also help consumers of these exploitable devices/firmwares by Updating Patched firmware using CWMP/TR-069 and some scripting. Hopefully, this possible exploit will be resolved by Airtel Broadband India, until then, 450TC1 users, never use WEP PSK for SSID1 and change Default admin credentials.
Hope this helps and Cheers 🙂 | Your feedback is highly appreciated.
WaheGuru G Ka Khalsa, WaheGuru G Ki Fateh
Copyright © 2013
For copyright purposes, VirtualizationMaximus.com is not in the public domain. The fact that this blog owner publishes an RSS feed does not grant any rights for republication or re-use of the material except in the manner described below.
All content in this blog created by the blog owner and his guest authors is the property of the blog owner and his guest authors and protected by international copyright laws and cannot be stored on any retrieval system, reproduced, reposted, displayed, modified or transmitted in any form, electronic or otherwise without written permission of the copyright owner except as noted below.
A brief excerpt of content that does not exceed 128 words or 512 characters may be quoted as long as a link is provided back to the source page on this blog and authorship is properly attributed.